Credentials inventory for GitLab.com
DETAILS: Tier: Ultimate Offering: GitLab.com
- Introduced on GitLab.com in GitLab 17.5.
As a GitLab.com top-level group owner, you are responsible for the overall security of your groups and projects. To assist, GitLab provides an inventory of all the credentials that can be used to access your groups and projects.
This page describes how to manage the credentials inventory for GitLab.com. To manage credentials on GitLab self-managed, see Credentials inventory for GitLab self-managed.
In the credentials inventory, you can view:
- For enterprise users:
- Personal access tokens (PATs).
- SSH keys.
You can also:
- Revoke a personal access token.
- Delete a user's SSH key.
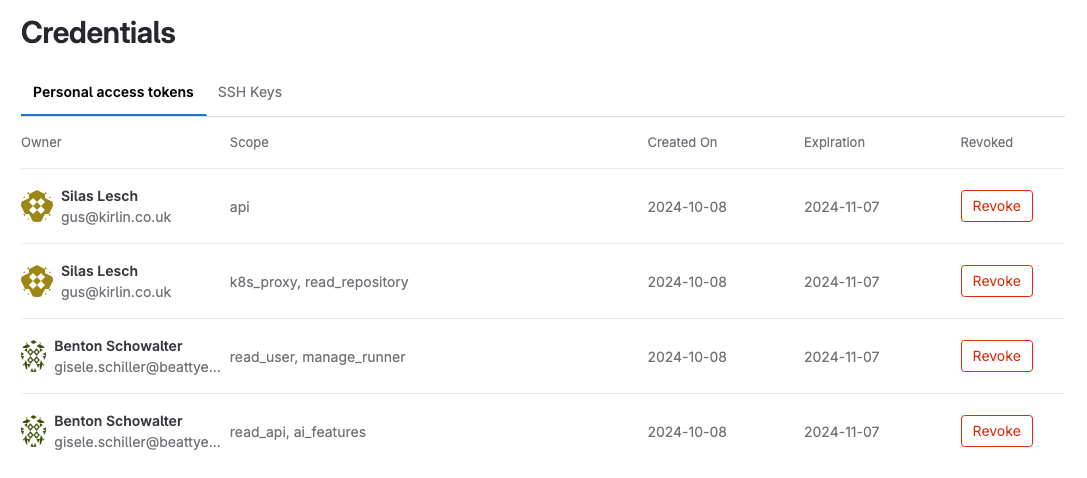
- View the following information about access tokens:
- Who they belong to.
- Their access scope.
- Their usage pattern.
- When they:
- Expire.
- Were revoked.
Revoke a user's personal access token
You can revoke an enterprise user's personal access token.
- On the left sidebar, select Secure.
- Select Credentials.
- By the personal access token, select Revoke.
If a Revoke option is not available, the token might already be revoked or have expired, or have an expiration date set.
| Token state | Revoke option displayed? | Comments |
|---|---|---|
| Active | Yes | Allows administrators to revoke the PAT, such as for a compromised account |
| Expired | No | Not applicable; token is already expired |
| Revoked | No | Not applicable; token is already revoked |
When a PAT is revoked from the credentials inventory, the instance notifies the user by email.
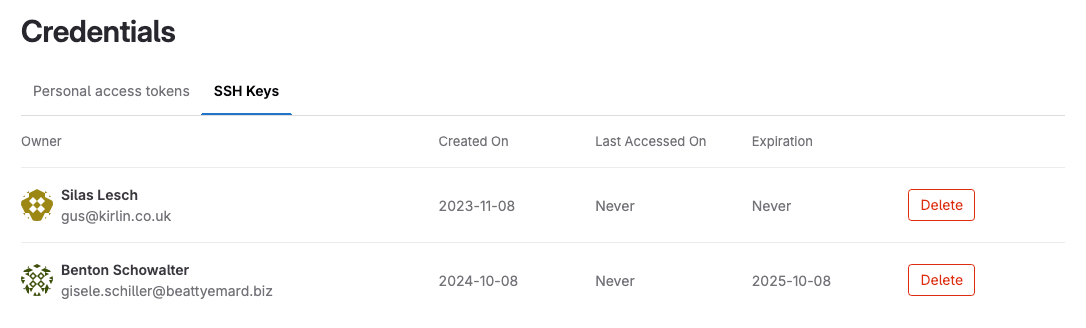
Delete a user's SSH key
- On the left sidebar, select Secure.
- Select Credentials.
- Select the SSH Keys tab.
- By the SSH key, select Delete.
The instance notifies the user.
Revoke a project or group access token
Credentials inventory on GitLab.com does not support viewing or revoking project or group access tokens. Issue 498333 proposes to add this feature.