Merge request approvals
- Tier: Free, Premium, Ultimate
- Offering: GitLab.com, GitLab Self-Managed, GitLab Dedicated
To set up a review process for changes in your project, configure merge request approvals. They help to ensure that changes are reviewed before they're merged into your project. You can configure approvals to be optional or required, depending on your project's needs and GitLab tier.
-
GitLab Free allows all users with at least the Developer role to approve merge requests. These approvals are optional and don't prevent merging without approval.
-
GitLab Premium and GitLab Ultimate provide you with more flexibility to:
-
Create required rules about the number and type of required approvals.
-
Create a list of Code Owners for specific files.
-
Configure approvals for the entire instance.
-
Configure group merge request approval settings.
Support for group merge request approval settings is tracked in epic 4367.
-
Configure approval rules
Prerequisites:
- You must have at least the Developer role for the project.
To configure approval rules:
- Go to your project's Settings > Merge requests.
- Go to the Merge request approvals section.
- Set up your desired rules.
You can also configure:
- Additional merge request approval settings for more control of the level of oversight and security your project needs.
- Merge request approval rules with the Merge request approvals API.
For more information on configuring rules, see Approval rules.
Required approvals
- Tier: Premium, Ultimate
- Offering: GitLab.com, GitLab Self-Managed, GitLab Dedicated
Required approvals enforce code reviews by specified users. Without these approvals, merging is not possible.
Use cases include:
- Enforce review of all code that gets merged into a repository.
- Specify reviewers and a minimum number of approvals.
- Specify categories of reviewers, such as backend, frontend, quality assurance, database, or documentation.
- Use the Code Owners files to determine reviewers.
- Require approval for declining test coverage.
- GitLab Ultimate: Require security team approval for potential vulnerabilities.
View approval status
Version history
- More granular approver display introduced in GitLab 17.9 with a flag named
mr_approvers_filter_hidden_users. Enabled by default.
You can see the approval status of a merge request in two places. On the merge request itself and in the list of merge requests for your project or group.
For a single merge request
Eligible approvers can view the approval status on a single merge request.
To view the approval status:
-
On the left sidebar, select Search or go to and find your project.
-
Go to Code > Merge requests and find your merge request.
-
To view the merge request, select its title.
-
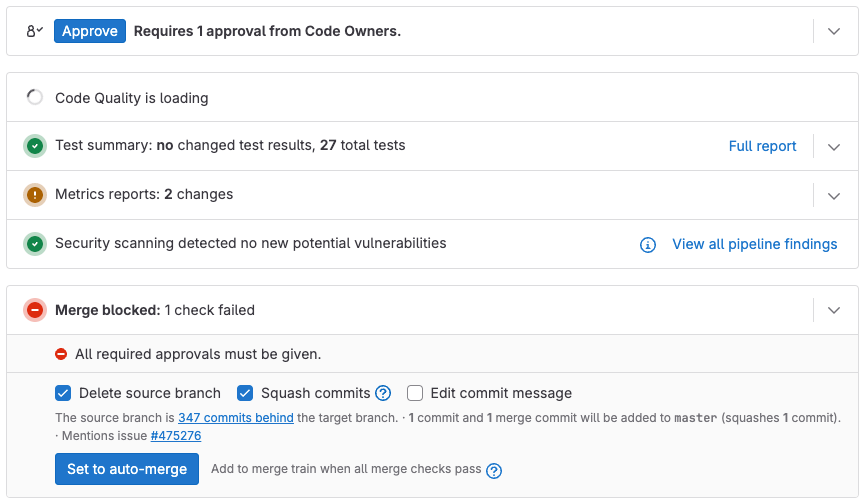
Go to the merge request widget to see the approval status. In this example, you can approve the merge request:
The widget displays one of these statuses:
- Approve: The merge request needs more approvals.
- Approve additionally: The merge request has the required approvals.
- Revoke approval: You have already approved the merge request.
To check if your approval satisfies Code Owner requirements, select Expand eligible approvers ({chevron-lg-down}).
If you have enabled the mr_approvers_filter_hidden_users feature flag, introduced in GitLab 17.9,
approver visibility depends on your project membership, and group privacy:
- Project members see all approvers.
- Project non-members see:
- All approvers, if the approvers are all from public groups.
- No information about approvers, if any of the approvers are from private groups.
In the list of merge requests
The list of merge requests for your project or group shows the approval status for each merge request:
| Example | Description |
|---|---|
 |
Required approvals are missing. ({approval}) |
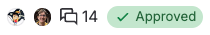 |
Approvals are satisfied. ({check}) |
 |
Approvals are satisfied, and you are one of the approvers. ({approval-solid}) |
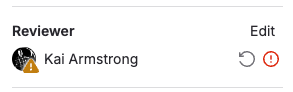
Individual reviewer status
To see the review and approval status for each reviewer:
- Open the merge request.
- Check the right sidebar.
Each reviewer's status is shown next to the their name.
-
{dash-circle} Awaiting review
-
{status_running} Review in progress
-
{check-circle} Approved
-
{comment-lines} Reviewer commented
-
{status_warning} Reviewer requested changes
To re-request a review, select the Re-request a review icon ({redo}) next to the user.
Approve a merge request
Eligible approvers can approve merge requests in two ways:
- Select Approve in the merge request widget.
- Use the
/approvequick action in a comment.
Approved merge requests display a green check mark ({check-circle-filled}) next to the user's name in the reviewer list. After a merge request receives the required approvals, it is ready to merge, unless it's blocked due to:
Prevent author approval
To prevent merge request authors from approving their own work, enable the Prevent approval by author setting.
Approval rule changes
If you enable approval rule overrides, changes to default approval rules don't affect existing merge requests, except for target branch changes.
Invalid rules
Version history
- Introduced in GitLab 15.1.
-
Changed in GitLab 15.11 with a flag named
invalid_scan_result_policy_prevents_merge. Disabled by default. -
Generally available in GitLab 16.2. Feature flag
invalid_scan_result_policy_prevents_mergeremoved.
GitLab marks approval rules as Auto approved when they're impossible to satisfy, such as when:
- The only eligible approver is the merge request author.
- No eligible approvers are assigned to the rule.
- The required approvals exceed the number of eligible approvers.
These rules are automatically approved to unblock merge requests, unless you created rules through a merge request approval policy.
Invalid policy-created rules:
- Display as Action required.
- Are not automatically approved.
- Block affected merge requests.